Bitonic is introduced and a theorem is proved. The algorithm of bitonic merge-sort is given.
介绍了二分序列的概念和定理证明,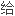
 了利用二分归并进行排序的算法及实
了利用二分归并进行排序的算法及实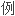 .
.
 算;
算; 算的;
算的; 算;
算; 算;
算; ]调度算法
]调度算法
 式算法;探试算法
式算法;探试算法 ]滤波算法;筛选算法
]滤波算法;筛选算法 算机程序法
算机程序法Bitonic is introduced and a theorem is proved. The algorithm of bitonic merge-sort is given.
介绍了二分序列的概念和定理证明,
 了利用二分归并进行排序的算法及实
了利用二分归并进行排序的算法及实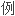 .
.
Given are 2 upvalue algorithms and a curve automatic matching method.
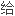
 了上提值的2种
了上提值的2种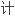 算方法和曲线的匹配方法。
算方法和曲线的匹配方法。
The security of encryption algorithms depends heavily on the computational infeasibility of brute force attack.
加密算法的安全性很大程度上取决于暴力破解的不可行性。
Bicubic rescale algorithm shrinks video to small screen size in best possible quality.
使用双三插值运算来修改画面大小,使得画质得到尽可能的保证。
A speech quality evaluation algorithm based on efficient psychoacoustics model,EPM-SQE,was proposed.
提 了一种高效心理声学模型语音质量评价(EPM-SQE)算法。
了一种高效心理声学模型语音质量评价(EPM-SQE)算法。
Traditional rate control algorithm is not fit to be used in transcoder in wireless environment.
摘要传统的码率控制算法不适合于无线环境中转码器的码率控制。
Dahlin algorithm combined with Cascade control (Dahlin-Cascade control) was put forward and used in practice.
运行结果表明,该控制方法能够很好地满足工艺要求。
Proposes pictureencryption algorithm based on the double unidimensional chaos system.
摘要 提 了一个基于双一维混沌系统的图像加密算法。
了一个基于双一维混沌系统的图像加密算法。
Screw compensation algorithm including coning and sculling compensations reduces the noncommutable error caused by rigid body .
设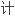 的螺旋补偿算法包括了传统的圆锥补偿和划船补偿,有效地减小了刚体转动的不可交换性误差。
的螺旋补偿算法包括了传统的圆锥补偿和划船补偿,有效地减小了刚体转动的不可交换性误差。
An algorithm was constructed to solve the least squares bisymmetric solution of a class of matrix equation.
摘要构造了一种迭代法求一类矩阵方程的最小二乘双对称解。
A new algorithm for tracing equiangular curves is presented to improve the machining quality of free-form surfaces.
为了提高自由曲面加工质量,提 一种等斜率曲线跟踪算法。
一种等斜率曲线跟踪算法。
And it gives the model of investment diversification of venture capitaland uses skiagraphy algorithm to solve it.
建立了风险投资分散模型,并运用投影算法对其进行求解。
A local search algorithm for minimizing a nondecreasing supermodular set function is presented,and its performance guarantee is probed.
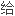
 了求解一类具有简单约束的上模集函数最小值问题的一种局部搜索法,并讨论了所
了求解一类具有简单约束的上模集函数最小值问题的一种局部搜索法,并讨论了所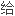 算法的性能保证。
算法的性能保证。
An approximation algorithm is presented for minimizing a nondecreasing supermodular set function, and its performance guarantee is probed.
摘要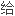
 了求解一类上模集函数最小值问题的一种近似算法,并讨论了所
了求解一类上模集函数最小值问题的一种近似算法,并讨论了所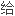 算法的性能保证。
算法的性能保证。
This paper proposed an algorithm for finding critical value of normal population variance under unbiassed tests with uniform dominance.
本文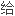
 了求正态总体方差的一致最优化无偏检验的临界值的算法。
了求正态总体方差的一致最优化无偏检验的临界值的算法。
Under mild assumptions on the inexactness, we can find an e-approximate solution of the SOCP by using this algorithm.
在相对不精确的假设下,利用该算法可找到二次锥规划的ε-近似解。
As compared with the hybrid tracking and the coplane four-point registration algorithms, the proposed algorithm is of higher registration accuracy.
与混合跟踪注册算法、共面四点注册算法相比,文中方法具有更高的精度。
In order to schedule all kinds of tasks, a novel tasks scheduling algorithm named dual-priority queues for uniprocessor is presented.
为了调度多种实时性的任务,提 了双优先级队列调度算法,用于调度每个处理器上的任务。
了双优先级队列调度算法,用于调度每个处理器上的任务。
Numerical simulations of laminar flow separation and reattachment occurred in an annular backstep passage are performed by the SIMPLER algorithm.
用SIMPLER算法对流过环形后台阶通道内的层流分离和再附着进行了数值模拟。
The effect that reduced the time of advect frames was achieved by flexible algorithm and reuse and copy relative pathlines.
采用弹性算法来控制种子的释放,通过重用、复制相关迹线来减少迹线的积分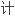 算,达到减少生成每帧图像所需的时间的效果。
算,达到减少生成每帧图像所需的时间的效果。
声明:以上 句、词性分类均由互联网资源自动生成,部分未经过人工审核,其表达内容亦不代表本软件的观点;若
句、词性分类均由互联网资源自动生成,部分未经过人工审核,其表达内容亦不代表本软件的观点;若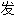 现问题,欢迎向我们指正。
现问题,欢迎向我们指正。